Hardening Monitoring & Analysis
Introduction
Default configuration of most devices (viz. operation systems, databases, routers, switches, etc.) is not designed with security as primary focus which leaves them vulnerable to security threats. Hardening is the process of enhancing device security through a variety of means which results in a much more secure server operating environment. KHIKA provides hardening compliance reports which precisely serve this purpose, to check devices regularly for compliance against hardening policies and pinpoint action items for corrective measures.
KHIKA collects hardening compliance data from devices on a daily basis which is then evaluated against standard pre-defined policies.
As part of its hardening compliance monitoring offering, KHIKA leverages its collection mechanism to gather the currently configured values/rules for hardening policies/parameters. For Servers (Linux & Windows), KHIKA uses the OSSEC Agent to run native OS commands (for Windows Servers - powershell commands are also used) to query the existing settings for various OS security parameters. The OSSEC Agent running on the servers queries the security parameter settings at configured intervals (typically every 24 hours) and send this information to the OSSEC Server running on KHIKA Data Aggregator.
The KHIKA Data Aggregator processes this information and forwards it to the KHIKA Application Server for indexing and storage. At the KHIKA Application Server, the current values for hardening policies/parameters are compared against their desired values as specified via the configured hardening compliance templates to provide a report that clearly denotes compliance and non-compliant policies per device.
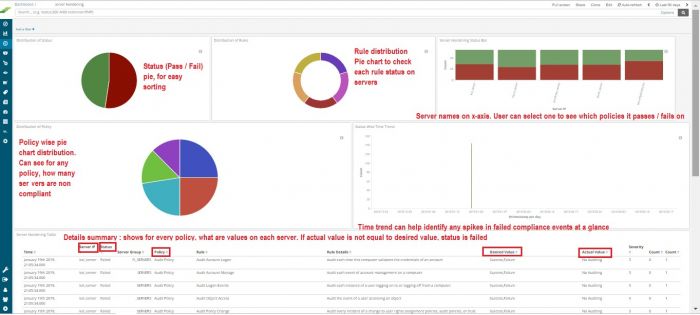
The best defense against security attacks is to ensure server hardening policies are implemented and up to date, to minimize these loopholes. The resultant reports depict the hardening posture for the respective device wherein each policy along with its compliance status is rendered on KHIKA dashboards.
Every organization tends to have its own compliance policies and hence KHIKA’s hardening compliance templates are customizable to meet the needs of any organization and enable hardening compliance posture assessment on a regular basis. Customization is available for customers who have implemented KHIKA as an on-premise setup.
Business Process flow for Linux Hardening
Following sequence explains the data flow and business process for Hardening analysis and monitoring using KHIKA :
- Hardening related data, values are collected into KHIKA using commands/scripts which run on servers via the Ossec Agent to get the hardening data into KHIKA.
- For Windows, Linux, Network devices and Oracle DB the polling interval is once every 24 hours.
- KHIKA processes this data and generates report dashboards which mention policy-wise the servers that are non compliant and what is their current state vis a vis the desired.
- This data is typically captured once in every 24 hours and dashboards are refreshed with current results.
Hardening Dashboard
Required Hardening Dashboard can be selected from the Dashboard list like other Dashboards
The next section is about data age in KHIKA, online and offline storage and Data Archival